Samsung claims that its Galaxy S25 series smartphones use post-quantum cryptography to protect data. It sounds like something out of science fiction, but what does it mean for us, ordinary users? Is it just another buzzword, or is it really the future of cybersecurity?
The fact is that current encryption methods only protect your passwords, bank transactions, and personal data because today's computers are too weak to hack. However, with the advent of quantum computers, this balance will change - algorithms that currently take thousands of years to crack can be broken in a matter of hours.
Samsung assures that the Knox Vault in Galaxy S25 is already ready for this threat - it uses post-quantum cryptography, which should withstand even the strongest attacks of the future. But how does it work, why is it important, and is this smartphone now better protected than the banking system?
Fast forward
- The threat of quantum computers: why can they hack everything?
- What is post-quantum cryptography?
- The future of post-quantum security: what's next?
- The bottom line.
The threat of quantum computers: why can they hack everything?
Modern security systems are based on the fact that it takes a long time to crack a complex password or encryption. For example, the standard 256-bit AES key is so secure that even the most powerful supercomputers will need billions of years to crack it. But this rule only works for classic computers.
And this is where quantum computers come into play - machines that do not calculate sequentially, but operate with quantum bits (qubits) that can simultaneously be in several states. This means that they can search for solutions in parallel, not one by one, like conventional computers.
How does this affect security?
Quantum computers can use special algorithms to break current ciphers. The most dangerous of these is the Shor algorithm, which can break RSA encryption (which is the basis for most banking systems, digital signatures, and VPN connections) many times faster than classical methods.
What does this mean for us?
- Our passwords, financial transactions, and personal files can be exposed to hackers.
- Traditional security systems (banking, corporate, government) will become vulnerable to attacks by quantum computers.
- Cybercriminals who gain access to such technology will be able to hack into security systems that are currently considered impregnable.
It should be noted here that not only criminals, but even states can use the "collect now, decrypt later" tactic to accumulate huge amounts of encrypted data, hoping that quantum computers of the future will be able to crack them. Thus, governments are already collecting information now, hoping to gain access to confidential communications, financial transactions, and personal data in the future through the power of quantum decryption.
When will this become a real problem?
For now, quantum computers are still at the experimental level, and they cannot yet break AES-256 encryption. However, large companies such as Google, IBM, and Chinese research centres are already testing quantum systems capable of performing millions of operations simultaneously. Experts predict that in 10-15 years, quantum attacks could become a real threat. Experts are already using a special term called Q-Day. This is a hypothetical moment when quantum computers will become powerful enough to break modern cryptographic algorithms (including RSA-2048), making many digital systems vulnerable.
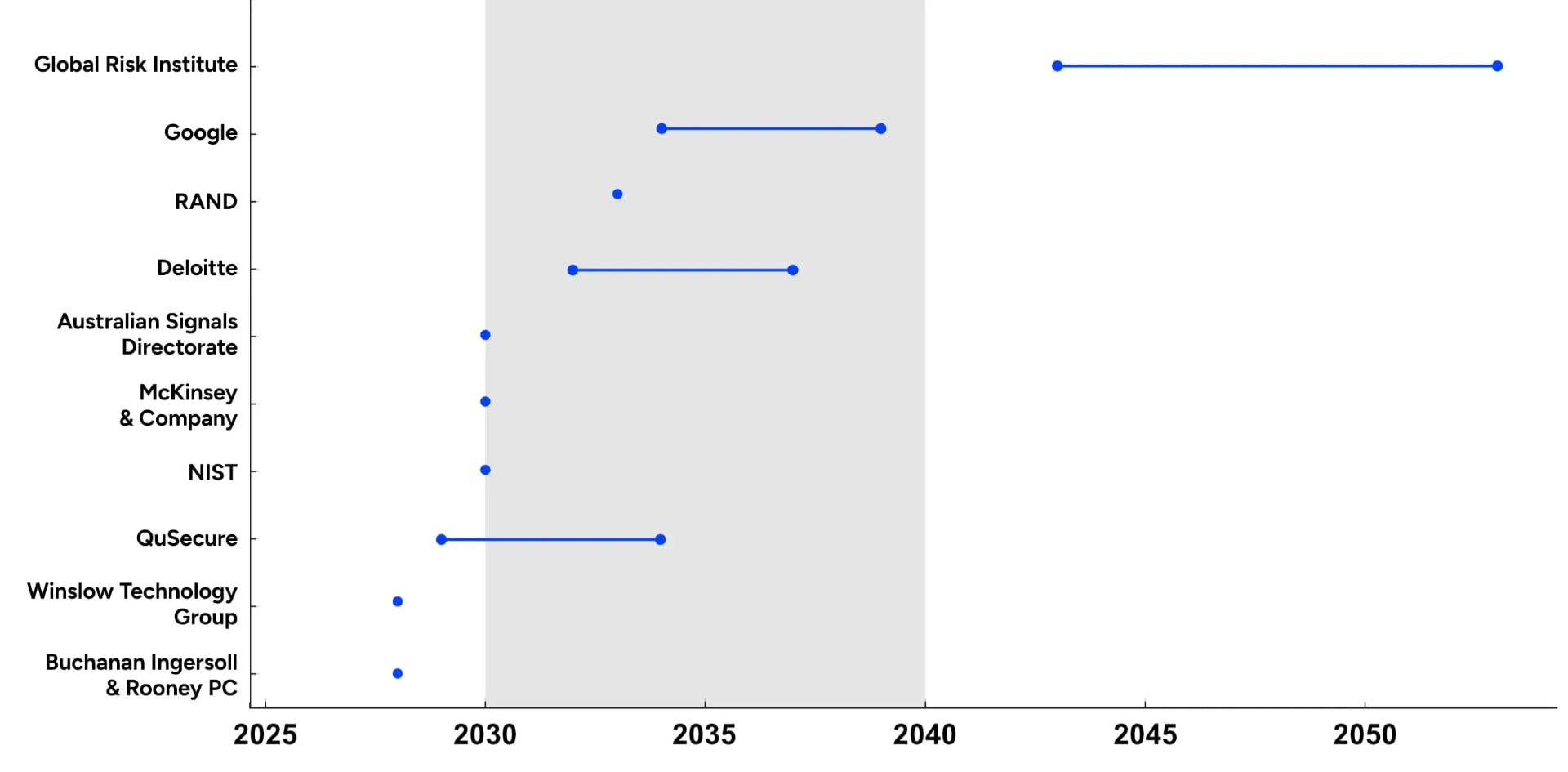
The year when Q-Day will come, according to experts from various companies. Illustration: secureworks.com
What is post-quantum cryptography?
If quantum computers can break modern encryption methods, what can we do to keep our data safe? The answer is Post-Quantum Cryptography (PQC). This is a new approach to information security that uses mathematical algorithms that are resistant even to attacks by quantum computers.
How does it work?
Unlike classical methods (RSA, AES, ECC), which rely on number factorisation or discrete logarithm (which is easily broken by quantum algorithms), post-quantum cryptography uses new mathematical approaches:
- Lattice-based cryptography is encryption based on complex geometric calculations in a multidimensional space.
- Code-based cryptography - methods that use the complexity of recovering information from encoded data.
- Multivariate polynomial cryptography - complex equations that a quantum computer cannot easily solve.
- Hash-based cryptography is a reliable method of digital signatures that is not subject to quantum attacks.
Why is it better?
- Resistance to quantum attacks - these algorithms were developed with the threats from quantum computers in mind.
- Reliability even in modern conditions - quantum machines are not so advanced yet, but PQC already provides a higher level of security.
- Scalability - post-quantum algorithms can be integrated into existing systems without changing the entire infrastructure.
The future of post-quantum security: what's next?
Quantum computers have not yet reached "full combat readiness", but it is not a question of "if", but "when". Already, scientists and large corporations are preparing for a world in which traditional encryption methods will become vulnerable.
When will quantum attacks become a real threat?
It is currently unknown, and estimates vary. According to some, a powerful quantum computer capable of breaking RSA-2048 may appear within 10-15 years. Other experts predict that this period could be even shorter - 5-7 years- if research is accelerated. For example, China is actively investing in quantum technologies and is already testing the first quantum encryption protocols for government communications.
How is the world preparing for the quantum age?
NIST (the US National Institute of Standards and Technology) is developing new post-quantum algorithms that will become the security standards of the coming years. The European Union is launching projects to protect digital signatures and banking transactions from quantum attacks. Tech companies are not waiting for this problem to explode either, but are already integrating post-quantum cryptography into their products. Apart from Samsung, we can mention Apple, which introduced its PQ3 protocol for its iMessage messenger in March 2024. The Signal messenger also announced the transition to post-quantum cryptography.
Do ordinary users need to worry?
Yes, because the data "hacked" today can be used even in 5-10 years. For example:
- If someone intercepts your encrypted files today, they can decrypt them when quantum attacks become a reality.
- Old passwords and encrypted correspondence may be revealed in the future if they are not protected by post-quantum algorithms.
- Your banking history, financial transactions, and even digital assets could be at risk from hackers.
Bottom line.
There's no doubt that even the RSA-2048 protocol can be cracked by quantum computers - it's just a matter of time. However, the exact time when such capabilities will be available is still a matter of debate, and there is no specific date when this will happen. However, it is a threat right now, as attackers can accumulate even encrypted confidential data to hack it in the future. Humanity already has an answer to the question "what to do" - to switch to new, more sophisticated encryption algorithms, which are commonly called "post-quantum cryptography". These are mathematical algorithms that are resistant even to attacks by powerful (compared to modern supercomputers) quantum computers. This transition to post-quantum cryptography should begin now, as the upgrade of security systems will take years. Therefore, we will hear the phrase "post-quantum cryptography" more and more often.
